Digital Signatures vs Traditional Signatures in Cryptocurrency
 Feb, 25 2025
Feb, 25 2025
Digital Signature Security Calculator
Security Estimator
Calculate the security level of digital signatures based on key size and algorithm type. This tool demonstrates how different signature schemes provide varying levels of protection against cryptographic attacks.
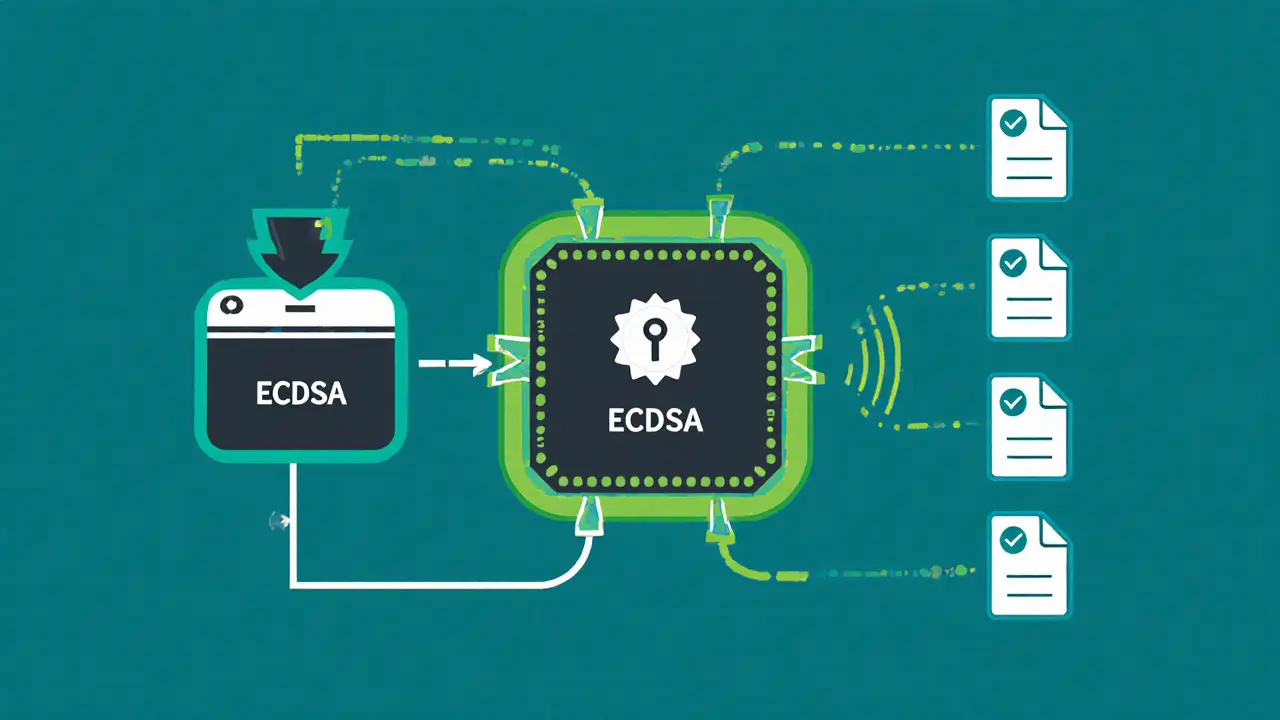
When you hear Digital Signatures is a cryptographic method that links a signer’s private key to a digital message, providing mathematical proof of authenticity. you probably picture Bitcoin, smart contracts, or a fast, tamper‑proof transaction. Traditional Signatures is a handwritten mark made with a pen, historically used to endorse paper documents. In the crypto world the two approaches sit on opposite ends of a security spectrum, and understanding their differences can save developers, investors, and regulators a lot of headaches.
How Digital Signatures Are Created and Verified
Digital signature creation follows a three‑step routine:
- Hash the transaction data with a cryptographic hash function (e.g., SHA‑256). The hash condenses the data to a fixed‑size fingerprint.
- Encrypt the hash using the signer’s private key via an algorithm such as ECDSA (Elliptic Curve Digital Signature Algorithm). The result is the signature.
- Broadcast the signed transaction to the network.
Verification is equally simple for a node:
- Retrieve the public key associated with the sender’s address.
- Re‑hash the original payload.
- Decrypt the signature with the public key and compare the result to the freshly computed hash.
If the two hashes match, the network knows the transaction came from the holder of the private key and that the payload has not been altered.
How Traditional Handwritten Signatures Work
A handwritten signature is a physical imprint of a person’s writing style. Its authenticity is judged by comparing the mark on a document to a known specimen. Experts look at stroke pressure, slant, speed, and the visual rhythm of the letters. The process is inherently subjective-different examiners can reach different conclusions, especially when the handwriting is ambiguous or the document has aged.
Because the verification relies on human perception, the method is slow, costly, and vulnerable to skilled forgery. There is no built‑in cryptographic proof that the signer intended to approve the exact content of the document; a signer could claim they never saw the final version.
Core Differences: Security, Non‑Repudiation, and Tamper Resistance
| Aspect | Digital Signatures | Traditional Signatures |
|---|---|---|
| Authentication | Public‑key cryptography verifies identity | Visual comparison by an expert |
| Non‑repudiation | Mathematical proof tied to private key | Weak - can be disputed or forged |
| Tamper evidence | Any change breaks the hash, invalidating the signature | Only obvious physical alterations are detectable |
| Scalability | Automated verification can handle millions of signatures per second | Manual review limits throughput |
| Implementation cost | Initial PKI setup, then low marginal cost | Requires handwriting experts and forensic labs |
The table makes it clear why blockchain protocols have adopted digital signatures as a security cornerstone while traditional signatures remain useful only for paper contracts outside the digital realm.
Signature Schemes Common in Crypto
Most public blockchains use ECDSA because its elliptic‑curve math gives strong security with short keys (typically 256 bits). Bitcoin, Ethereum, and many altcoins rely on it for everyday transactions.
Newer schemes are gaining traction:
- Schnorr signatures - adopted by Bitcoin’s Taproot upgrade (BIP‑340). They are non‑malleable and enable key aggregation, allowing many participants to produce a single, compact signature.
- BLS signatures - used in projects like Ethereum 2.0 and some privacy‑focused coins. They support signature aggregation across entire blocks, cutting bandwidth by roughly 50 %.
- EdDSA (Ed25519) - favored by newer chains for its deterministic nature and fast verification.
RSA and DSA still appear in legacy systems, but their larger key sizes (1024‑2048 bits) make them inefficient for high‑throughput networks.
Why Digital Signatures Enable Crypto‑Specific Features
Because a signature is just a piece of data that can be programmatically checked, developers can build complex protocols that are impossible with pen‑and‑paper:
- Multi‑signature wallets - Multiple private keys must sign a transaction, but Schnorr aggregation makes the on‑chain footprint look like a single‑signature spend.
- Threshold signatures - A group of validators collectively controls a key; any subset meeting the threshold can sign.
- Ring signatures - Used by privacy coins (e.g., Monero) to hide the actual signer among a set of possible signers.
- Smart contract verification - Contracts can check a signature without human input, enabling automatic escrow, voting, and DAO governance.
All of these rely on the certainty that the signature can’t be forged without the private key, a guarantee that handwritten signatures simply cannot provide in a decentralized network.
Implementation Considerations for Developers
Adopting digital signatures means setting up a Public Key Infrastructure (PKI). The steps are:
- Generate a key pair (private + public) using a secure library (e.g., OpenSSL, libsecp256k1).
- Store the private key in a hardware security module (HSM) or a well‑protected wallet.
- Publish the public key as part of an address or a DID (Decentralized Identifier).
- Integrate signature verification into your transaction processing pipeline.
Common pitfalls include reusing the same nonce in ECDSA (which leaks the private key) and failing to protect the private key against malware. Using deterministic signatures (as EdDSA does) eliminates the nonce‑reuse risk.
Future Directions: Post‑Quantum Signatures and Decentralized Identity
Quantum computers threaten elliptic‑curve schemes because Shor’s algorithm can solve the discrete‑log problem efficiently. Researchers are already standardising post‑quantum alternatives like CRYSTALS‑Dilithium and Falcon. Major blockchain consortia plan migration paths that keep current assets safe while upgrading to quantum‑resistant signatures.
At the same time, decentralized identity projects (e.g., Hyperledger Indy, Microsoft ION) blend digital signatures with self‑sovereign IDs, giving users control over who can verify their credentials without a central authority.
Quick Checklist - Deciding Between Digital and Traditional Signatures
- Do you need automated, high‑throughput verification? → Digital.
- Is the document purely physical and governed by local handwriting‑expert law? → Traditional.
- Is non‑repudiation critical for dispute resolution? → Digital wins.
- Do you require multi‑party collaboration (multi‑sig, threshold, ring)? → Digital signatures only.
- Are you comfortable managing cryptographic keys and PKI? → If not, consider a managed digital‑signature service.
Bottom Line
In the cryptocurrency ecosystem, digital signatures are not just a convenience-they are the security backbone that makes decentralized trust possible. Traditional signatures still have a place in the legal world, but they lack the mathematical guarantees, speed, and programmability that blockchain demands. Whether you’re building a new token, a DAO voting system, or a simple wallet, choosing the right signature scheme will shape the safety, scalability, and user experience of your project.

Can I use a handwritten signature to approve a crypto transaction?
No. A blockchain only accepts data that it can verify mathematically. Handwritten signatures cannot be interpreted by the network without a trusted off‑chain oracle, which defeats decentralisation.
What is the main advantage of Schnorr over ECDSA?
Schnorr signatures are linear, allowing multiple public keys to be aggregated into a single signature. This reduces transaction size and hides the number of signers, a feature ECDSA lacks.
Are digital signatures legally binding?
Yes, in many jurisdictions. In the U.S. the ESIGN Act and in the EU the eIDAS regulation give electronic signatures the same legal weight as handwritten ones, provided they meet specific technical standards.
How do I protect my private key from theft?
Store it in hardware wallets, use multi‑factor authentication for software wallets, and never expose the key on internet‑connected devices. Consider Shamir’s Secret Sharing for high‑value assets.
Will quantum computers make current crypto signatures obsolete?
Potentially, yes. Elliptic‑curve schemes could be broken, which is why the community is already testing post‑quantum algorithms like CRYSTALS‑Dilithium for future upgrades.
Derajanique Mckinney
October 25, 2025 AT 17:35Sheetal Tolambe
October 25, 2025 AT 18:57Pranav Shimpi
October 26, 2025 AT 05:51Kirsten McCallum
October 26, 2025 AT 22:59Henry Gómez Lascarro
October 27, 2025 AT 21:59james mason
October 28, 2025 AT 14:55gurmukh bhambra
October 28, 2025 AT 21:24Sunny Kashyap
October 29, 2025 AT 05:03Frech Patz
October 29, 2025 AT 19:14jummy santh
October 30, 2025 AT 05:09Anna Mitchell
October 30, 2025 AT 15:26Rosanna Gulisano
October 30, 2025 AT 23:38